NEW DELHI: Despite teaming up with the country’s top cybercrime units Ransomware attack continued AIIMS Sources in the servers and systems, security establishment said the chances of fully recovering from the damage caused by the malware were bleak and a “fresh start” appeared to be the way out.
CERT-IN (Indian Computer Emergency Response Team), C-DAC (Center for Development of Advanced Computing) and NIC (National Informatics Centre), apart from two intelligence agencies, were trying to restore the system, but were yet to achieve success even on the fifth day as AIIMS services remained on manual mode.
According to the sequence of events established so far, the primary and first backup servers of AIIMS were found to have crashed around 7 am on Wednesday. The first disruption was reported from the emergency lab when operators were unable to view reports in the system. Billing department and OPD counters soon reported the same error.
“The priority was to identify and isolate the infection. Weak firewalls, no back-up and outdated systems were contributing factors. Identifying the infection correctly was important because each ransomware has different varieties and each requires a different response,” said was A source.
The agencies then tried to “recover the lost data” through advanced recovery tools, but could not decrypt the files. During a ransomware attack, the actual files are usually deleted by the malware and replaced with an encrypted replica.
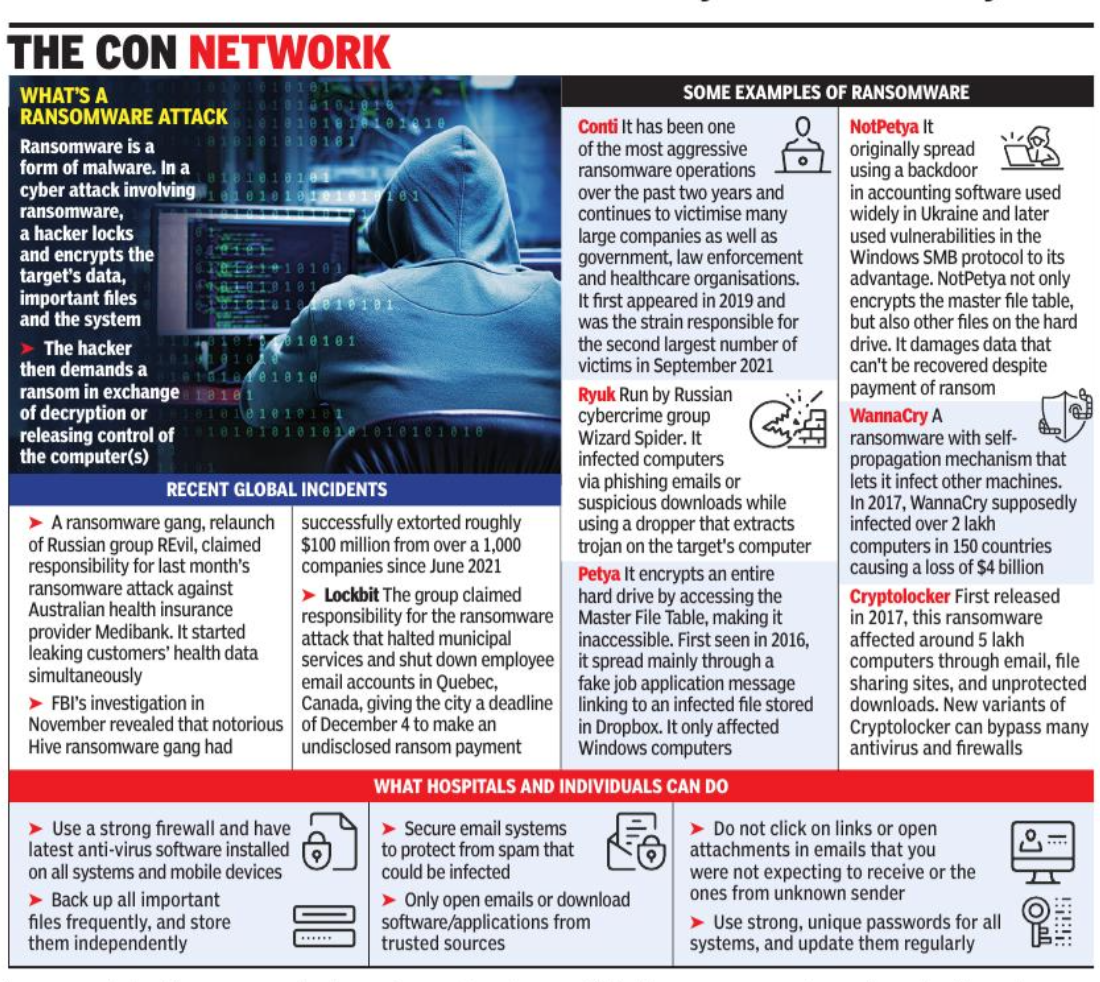
When asked if the ransomware was code-named Life, a new variant of the notorious ransomware WannaRen, was found on the infected server, officials said it was too early to draw conclusions. Police are investigating the case as cyber-terrorism and extortion. A major concern for investigators is potential data leakage as hackers usually start leaking information online if their demands are not met in time. Extortion also increases as victims try to salvage the situation.
Globally, ransomware attacks are wreaking havoc, especially since they are available as RAAS (ransomware-as-a-service) on the dark web where they can be purchased and (mis)used like apps without the necessary knowledge.
In early November, a ransomware group with suspected links to the notorious Russian ransomware gang, REvil, threatened to release the personal information of millions of customers of Australian health insurance service provider Medibank if ransom demands were not met. As the company refused to pay, the gang began publishing stolen records, including customers’ names, dates of birth, passport numbers and medical claims information.
The semiconductor chip manufacturing giant was hit by a ransomware attack in February this year and the attackers started leaking employee credentials online.
The government of Costa Rica recently declared a national emergency in response to a ransomware attack on the nation, which began in early April and brought the Ministry of Finance to its knees, affecting not only government services, but also the private sector engaged in imports. export
According to experts, ransomware targeting hospitals appeared to spread mainly through emails – often falsely claiming to be information or advice from a government agency, which prompted the recipient to click on an infected link or attachment.
In 2020, Interpol issued a warning to organizations at the forefront of the global response to the Covid-19 outbreak that have also become targets of ransomware attacks, designed to force them out of their critical systems to extort payments.
It found that cybercriminals were using ransomware to digitally hold hospitals and medical services hostage, preventing them from accessing critical files and systems until the ransom was paid. Interpol also issued “Purple Notices” to police in all 194 of its member countries warning of the growing threat of ransomware.